Delegate tasks to super users with laser precision – Microsoft 365
It is not uncommon these days to find IT leaders striving to lighten the load of their team members by delegating simple tasks to super users and business unit owners within their organization and Microsoft 365 environment. Redistribution of responsibilities frees up IT resources to deal with more complex issues and to allocate more time to operational innovations.
While Microsoft 365 has various default roles available and some capabilities to create custom roles, the permissions that make these up may be granting excess reach for certain single-task responsibilities.
For example, if you need to assign a user the ability to only read files in Teams with names that start with ‘Project’, then there is no native solution for this. Your options are limited to assigning the user to one of the Teams admin roles that encompass more than just reading files. And this will be for every Team in the tenant.
You can use Administrative units in the Azure Active Directory for each Team scope, but once you define them, you will be limited to using only these units and you will have to update them. Additionally, there are some premium licensing requirements.
Another option is to directly add a read-only permission for the user for each Team’s SharePoint site (i.e. the storage of the Team’s document library). Since this can only be done one site at a time, this may take a while, depending on how many Teams are involved.
sapio365 offers a simpler, non-disruptive, and more granular approach to creating roles and their scopes of action.
The role-based access control in sapio365 is applied independently from the roles available in Microsoft 365. Each feature and each view serve as permissions that are added to the role, which acts to compartmentalize sapio365’s functionality so that only the specified actions are allowed.
Let’s look at how to set up and assign a read-only role that targets Teams with names beginning with ‘Project’.
Create a custom role in sapio365 RBAC
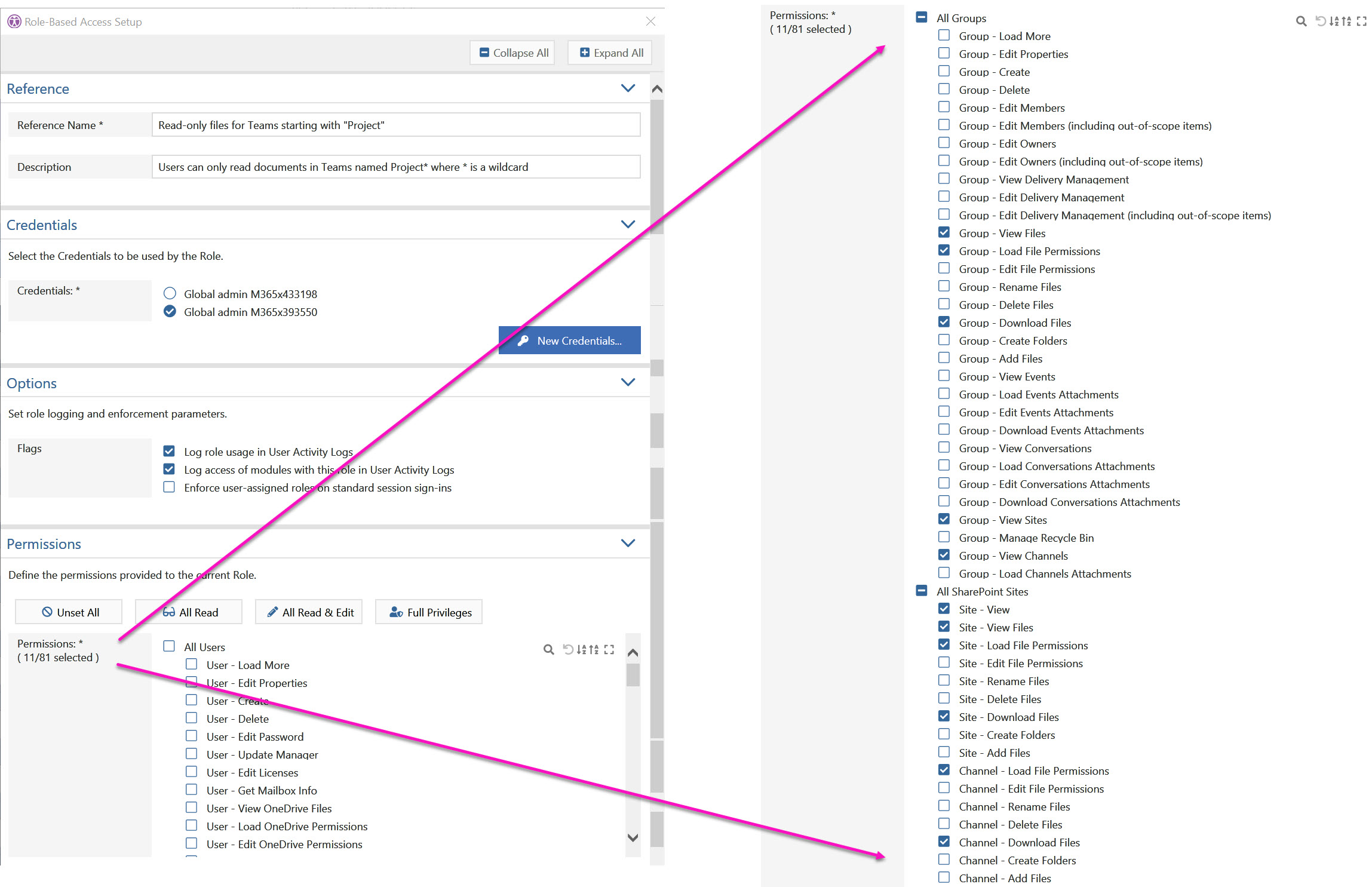
First we need to add credentials in sapio365. We can do this in the configuration panel of the role-based access control (RBAC) section. Of course, it’s important to use credentials that have the required Microsoft 365 permissions for the tasks we want to assign. So for this case I’m using those of the global admin.
Next, we create the role. Choose the credentials you want to use or create new ones. Then select the permissions/features you want to enable for sessions using this role.
Under ‘Options’, you can also choose if you want to record when delegates access sapio365 views. You can also oblige a delegate to use a role with his sapio365 session.
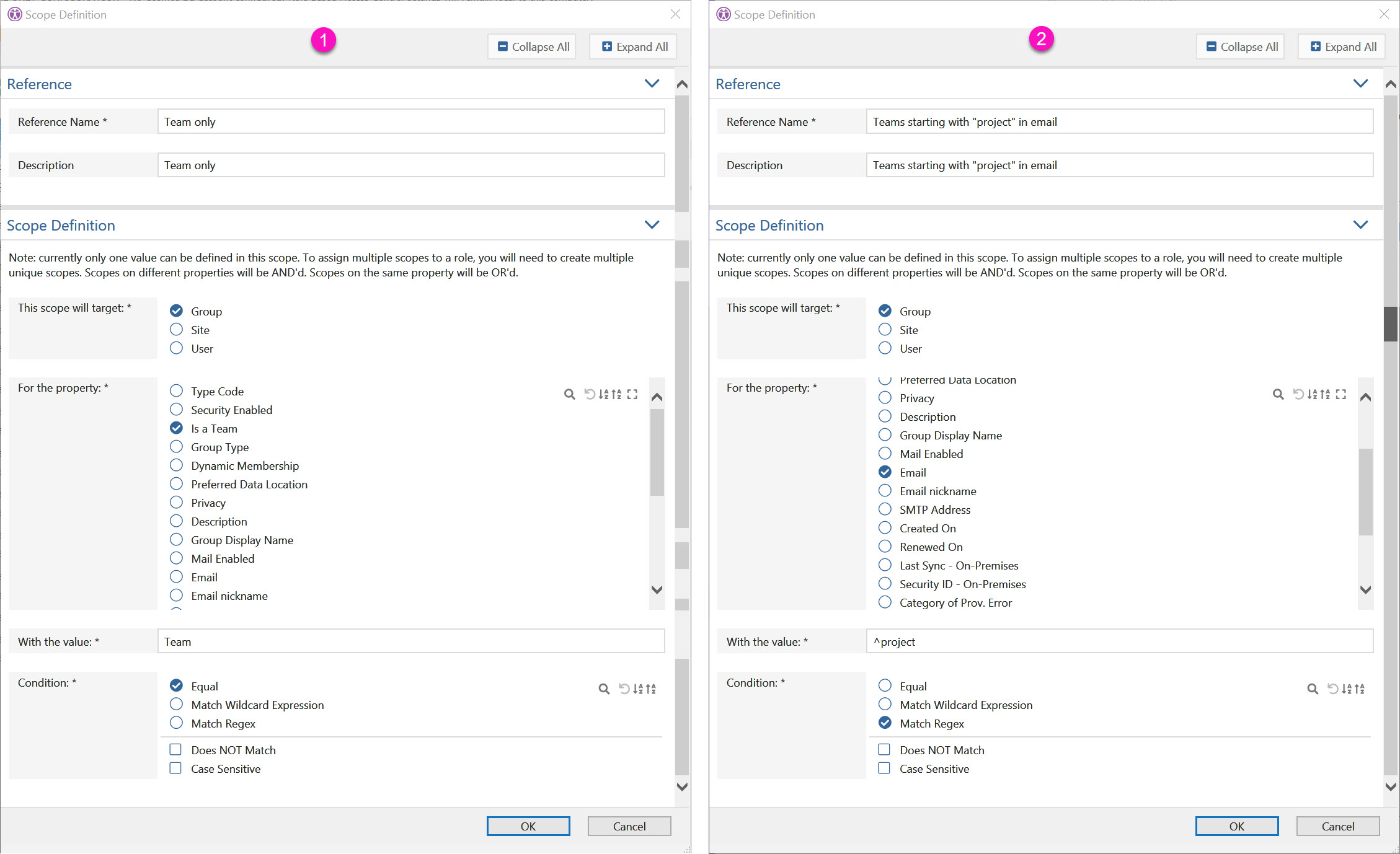
Next, we add scopes to that role.
I’ve created two scopes for groups. This will ensure that only Teams are shown [1], AND that their email starts with ‘project’ [2]. Both scopes must be assigned.
Next assign a user, in this case it’s Alex.
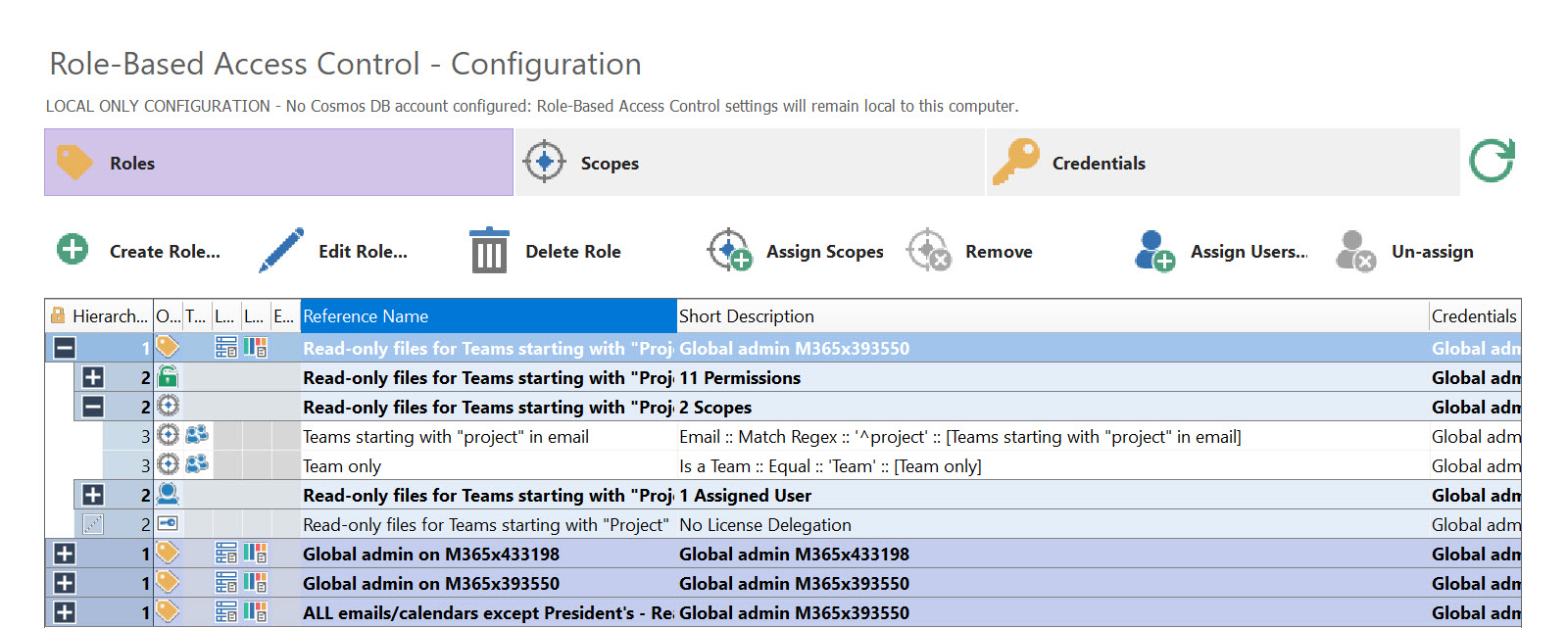
Finally, let’s look at what our role looks like. Note the 11 permissions we selected earlier, the scopes of action we defined, and the assigned user.
Suggestion: Add numbers to image for the three items being called to attention (permissions, scopes, assigned user)
What happens when the delegated user Alex signs into sapio365?
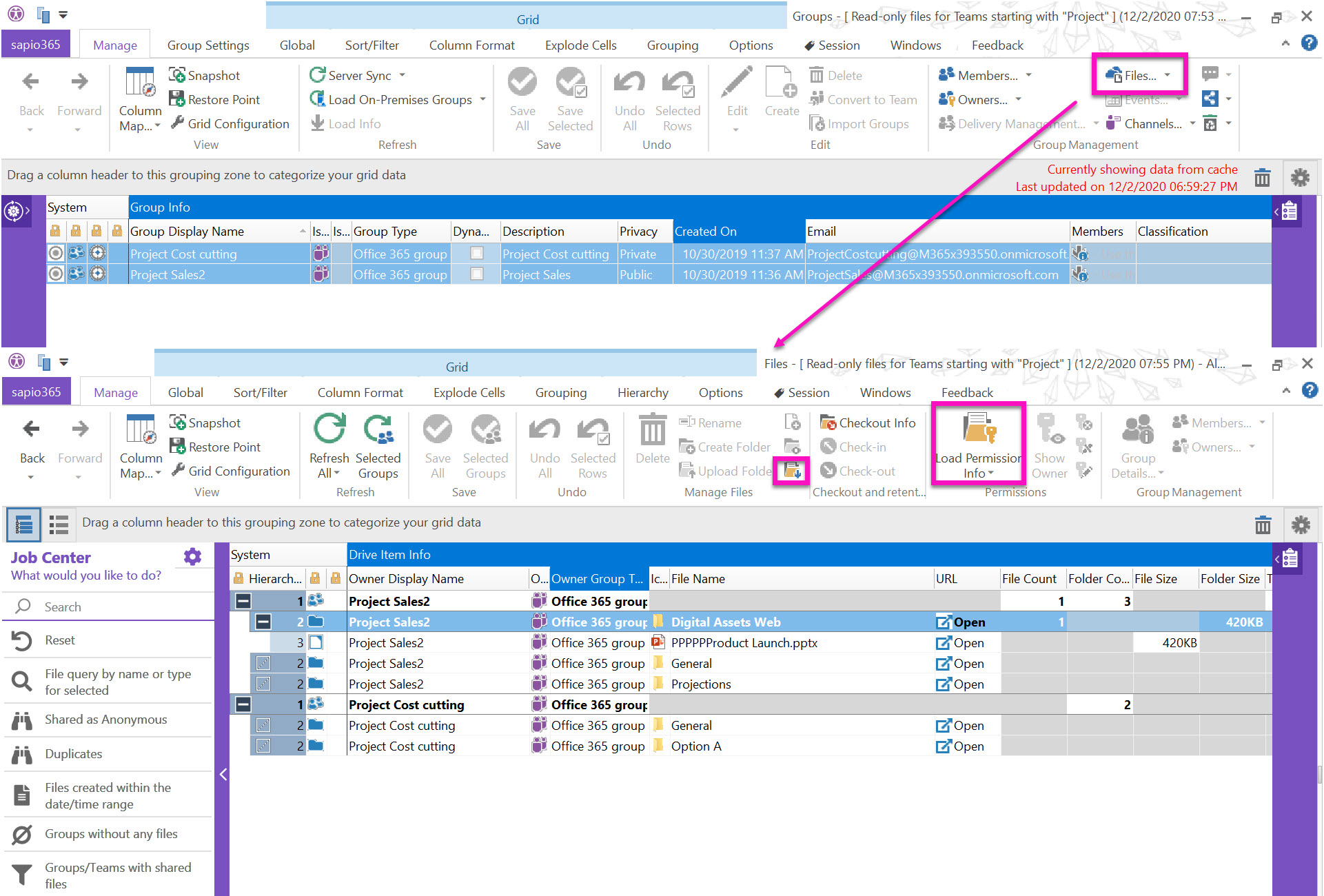
When Alex launches Groups, he will only see those Teams defined by the role we created (pictured below). He can then get a list of their files or access their channels (just in case some of these have private channels). Note that the buttons for members/owners are not off-limits, since that information is also generally accessible to all in Microsoft 365.
Once he’s accessed the file information for those Teams, Alex will only be able to view the file data or to download them. All other functions are disabled.
Audit sapio365 usage for the delegated user Alex
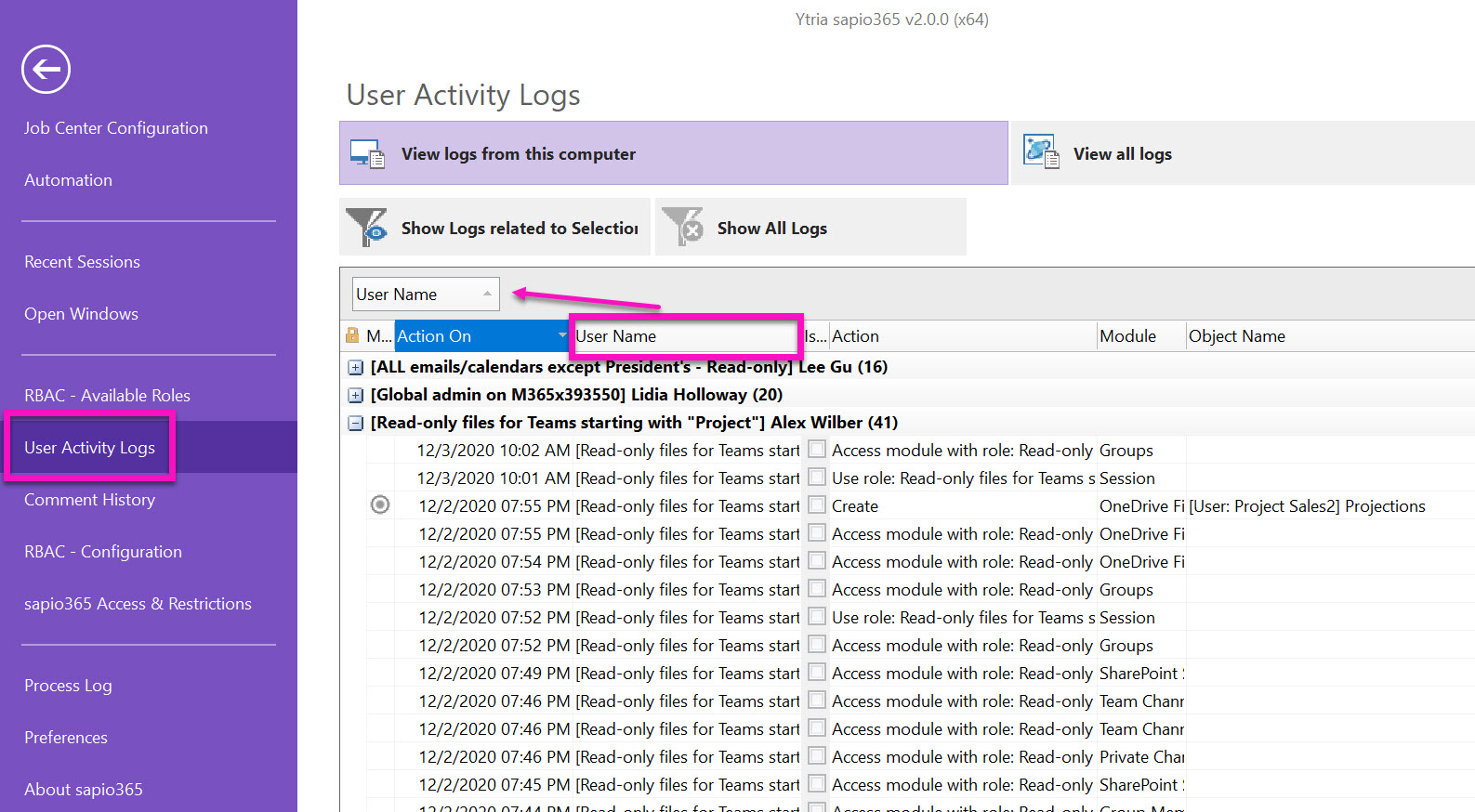
The global admin, or whomever has been appointed to monitor User Activity Logs in sapio365, can monitor what has been accessed by each delegate.
A quick grouping by user, and we can see what Alex has done and when it was done, while using that specific role. You can also see user activity in Microsoft Office 365 with Microsoft Office 365 audit logs. You can learn more about that here.
A note on using sapio365 RBAC:
Unless you are all using the same machine, a connection is needed to an Azure Cosmos DB account to use sapio365 RBAC and access sapio365 User Activity Logs from different machines.
You can set up Azure Cosmos DB in your own Azure subscription right from sapio365 with just a few steps.
Now that you know how to create a very specific role in sapio365 RBAC, you can delegate pretty much anything because both the roles and scopes of action can be as granular as you need them to be.
Next time we’ll look at how to automate the delegation of some common tasks with the Automation Jobs Library. This can be an even more convenient alternative to RBAC in sapio365.
No credit card required
Submit a comment