The Savvy Admin’s Guide to Audit Logs in Office 365
Many IT admins who are managing their organization’s Office 365 environment need more information about the activities occurring in their tenants. Audit logs in Entra ID (Azure Active Directory or Azure AD) are one way to gain the insights you need to better manage Microsoft 365. This guide will showcase the different types of Office 365 audit logs available and show you how to access and interpret these audit logs. Armed with this knowledge, you’ll be able to set up alerts, troubleshoot issues that arise, and leverage the logs to make informed decisions.
Introduction to Audit Logs in Office 365
Before we look at the different types of audit logs available within Microsoft 365, let’s learn what audit logs are and why they are important.
Audit logs provide a comprehensive record of activities within your Microsoft 365 environment. They are important for maintaining security and compliance by tracking user actions, system changes and attempts to access your network. Because they provide a detailed timeline of events, they allow you to recreate past actions, meet compliance requirements, identify potential security breaches and respond quickly to them.
Audit logs are part of a strong IT security strategy, providing valuable and sensitive information when you are troubleshooting or investigating a security issue. Beyond security, they are also important in proving compliance is being maintained.
Microsoft 365 IT admins can be proactive in managing their IT environment by running and analyzing audit logs regularly and by setting up automated alerts for suspicious or unusual activities, such as multiple failed login attempts or sudden file downloads.
Key benefits for administrators and organizations
- Audit logs offer IT admins more visibility and detail into user activity so you can track down the source of issues, identify the root cause of an issue and take measures to prevent future incidents.
- Audit logs are very helpful with compliance during external audits. Microsoft 365 IT admins get detailed records of user activity which can be used as evidence that regulatory requirements are being met.
- Audit logs encourage accountability because when every action is logged, a culture of responsibility is created, discouraging bad practices.
- The use and analysis of audit logs leads to better decision-making. These analyses uncover trends and patterns that lead to better allocation of IT resources and improved user experiences.
- By conducting an audit log search, IT admins to be more proactive. They can highlight unusual patterns so admins can address issues before they escalate.
Setting Up and Enabling Audit Logs
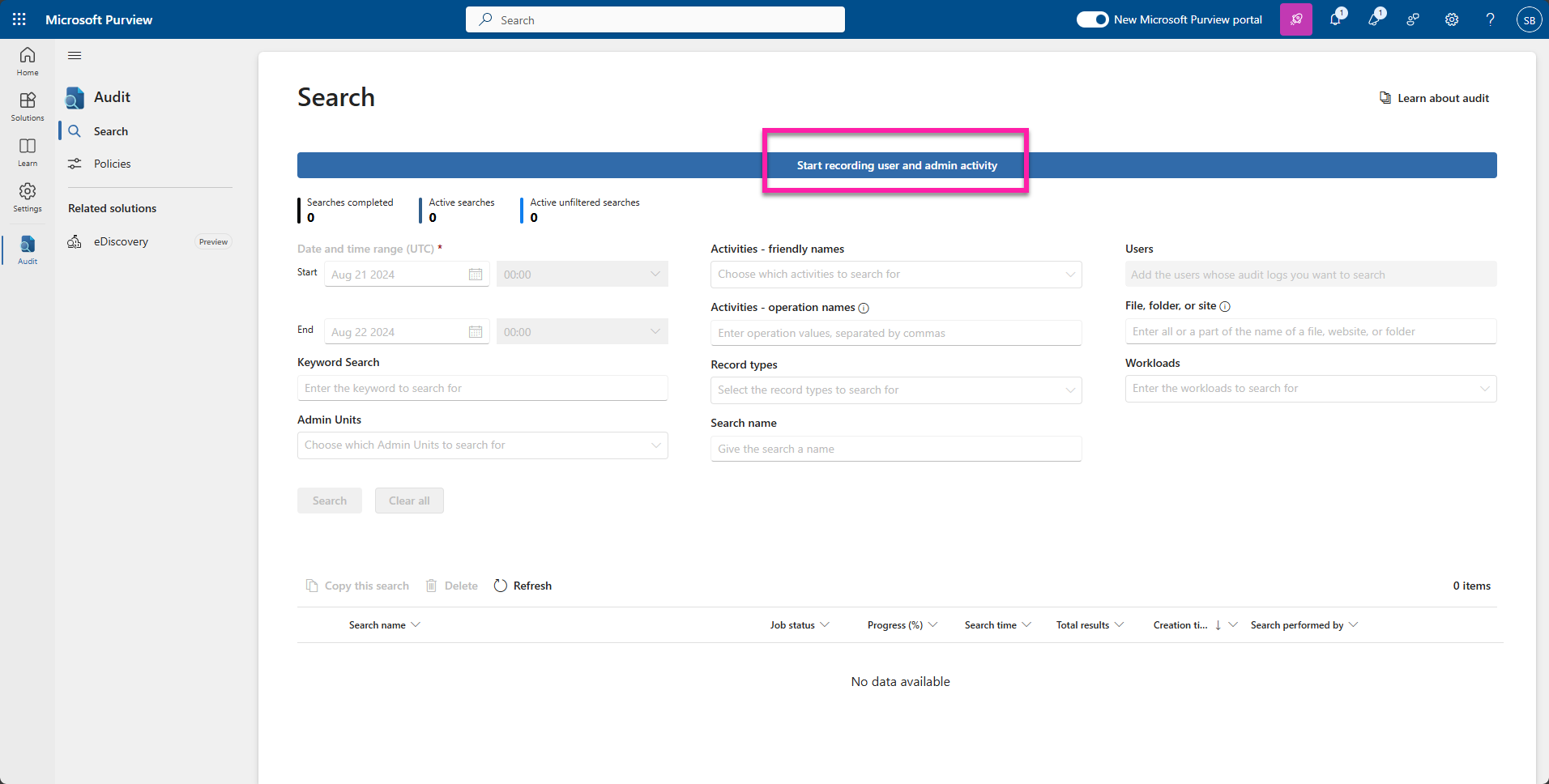
To start recording user activity, you will need to set up and enable Office 365 audit logs in Azure AD. Go to the Purview or Compliance Portal in the Microsoft 365 admin portal and look for the Audit section.
To make sure that audit logging is turned on, you must click on the Start Recording user and admin activities. Once enabled, you can start customizing what you would like recorded, depending on your organization’s needs and concerns.
You an also use Exchange Online PowerShell to turn on logging with the following cmdlet: Set-AdminAuditLogConfig -UnifiedAuditLogIngestionEnabled $true
When audit logging is enabled, you should verify that everything is working well by going to the Microsoft 365 Defender portal. Check for recent user activity, file access or other administrative changes in the audit log search. If data starts to populate, your audit logs are capturing the right information.
When your audit logs are enabled, you can start customizing what information you want recorded, setting up alerts and optimizing the configuration of your Office 365 audit logs.
You can also check if it’s on by running the following Exchange Online PowerShell cmdlet: Get-AdminAuditLogConfig | Format-List UnifiedAuditLogIngestionEnabled
Best practices for configuration
There are several best practices that strengthen overall IT security.
- Configure your alerts to notify you when specific actions happen. This can include alerts for suspicious activities like file access, account modifications, or deletions of large files.
- Make sure to regularly review your audit logs to ensure continuous monitoring. By checking your logs weekly for example, you will be able to spot trends and address issues before they become problems.
- Consider integrating your audit logs with a security information and event management system which can streamline threat detection across your Microsoft 365 environment.
Navigating the Office 365 Audit Log Interface
The Office 365 audit log interface is the tool that allows IT admins to monitor their environment, so knowing how to access and use this powerful feature is important.
There are a few tools you can choose to access your searchable log, depending on your security needs and workflow
Accessing audit logs can be done from the Microsoft Purview compliance portal, in the Audit section, under Solutions.
For admins who are focused on security, you can also use the Microsoft 365 Defender portal and go to the Audit section.
Finally, for IT admins who like to use PowerShell, you can leverage the Search-UnifiedAuditLog cmdlet for programmatic access and automation.
Understanding the audit log search interface
To extract your data, you use the audit log search interface, which has a user-friendly search form. From there you can choose criteria such as date ranges, user accounts, activities, as well as filters to narrow down your search results. The Activities dropdown menu offers a full list of auditable events across Microsoft 365 services.
Key components and features of the audit log dashboard
The audit log dashboard has features and audit settings designed to improve auditing. The main results pane displays your search results in a format that allows you to quickly scan and sort and then export for more in-depth reporting and analysis. Apply more filters to focus on a specific activity or user.
Types of Activities Tracked in Office 365 Audit Logs
You can customize what kinds of activities are recorded. The type of activities you choose to track will depend on your organization’s needs. For example, if you’re particularly concerned about data loss, you might focus on file and folder activities. On the other hand, if you want to track changes or accessed documents, you want to focus on user and admin activity. We’ll examine the key categories of activities that can be tracked in audit logs.
| Type of activities found in Audit Logs | Some activity examples |
|---|---|
| User activities | • Accessing a file • Deleting an email • Sharing a file • Forwarding an email |
| Admin activities | • Creating a group • Assigning a license • Assigning an admin role • Changing a security setting |
| Security and compliance activities | • Creating retention policies • Enabling litigation hold on an account • Changing SharePoint access settings |
| Application-specific activities (SharePoint, Exchange, Teams, etc.) | • Deleting a SharePoint site • Changing a mail rule • Creating a new Teams channel |
User activities
Tracking user activities will tell you how employees are using Microsoft 365 services. The audit logs will track typical user activities like accessing files, sharing and any modifications in OneDrive and SharePoint sites as well as email activities in Exchange Online, such as reading, forwarding and deleting messages. This can help you spot unusual patterns that could be a sign of data leaks or compromised accounts. Other high-risk activities that should be highlighted include changes to sharing permissions or mass downloads.
Admin activities
All changes made by Microsoft 365 IT administrators, including account modifications, permission updates and configurations changes, can be captured. There are certain activities that you should monitor more closely, such as the addition of new admins or changes in security settings. Reviewing these logs on a regular basis will help you detect unauthorized admin actions that could compromise security. Knowing admin activities are tracked will keep your IT team accountable.
Security and compliance activities
Audit logs on security and compliance activities track events related to data loss prevention, eDiscovery searches and retention policies, as well as activities from security features like Microsoft Defender. Enabling this type of audit logs will allow you to make sure your compliance policies are working and to identify security breaches early. This information can be used to adjust security settings.
Application-specific activities (SharePoint, Exchange, Teams, etc.)
Tracking application-specific activities helps keep track of user interactions with specific Microsoft 365 services. For example, in SharePoint, you can capture permission changes and when sites are created. In Exchange, you can log mailbox access and rule modifications, while in Teams, you can get insight into the creation of channels, file operations and meeting activities. With activities specific to applications, you should pay attention to external user invitation, changes to sharing settings, or any activities that could result in data exposure.
Performing Effective Audit Log Searches
Let’s examine strategies that can help improve effectiveness and efficiency so you can gain valuable insights from all the data that is available.
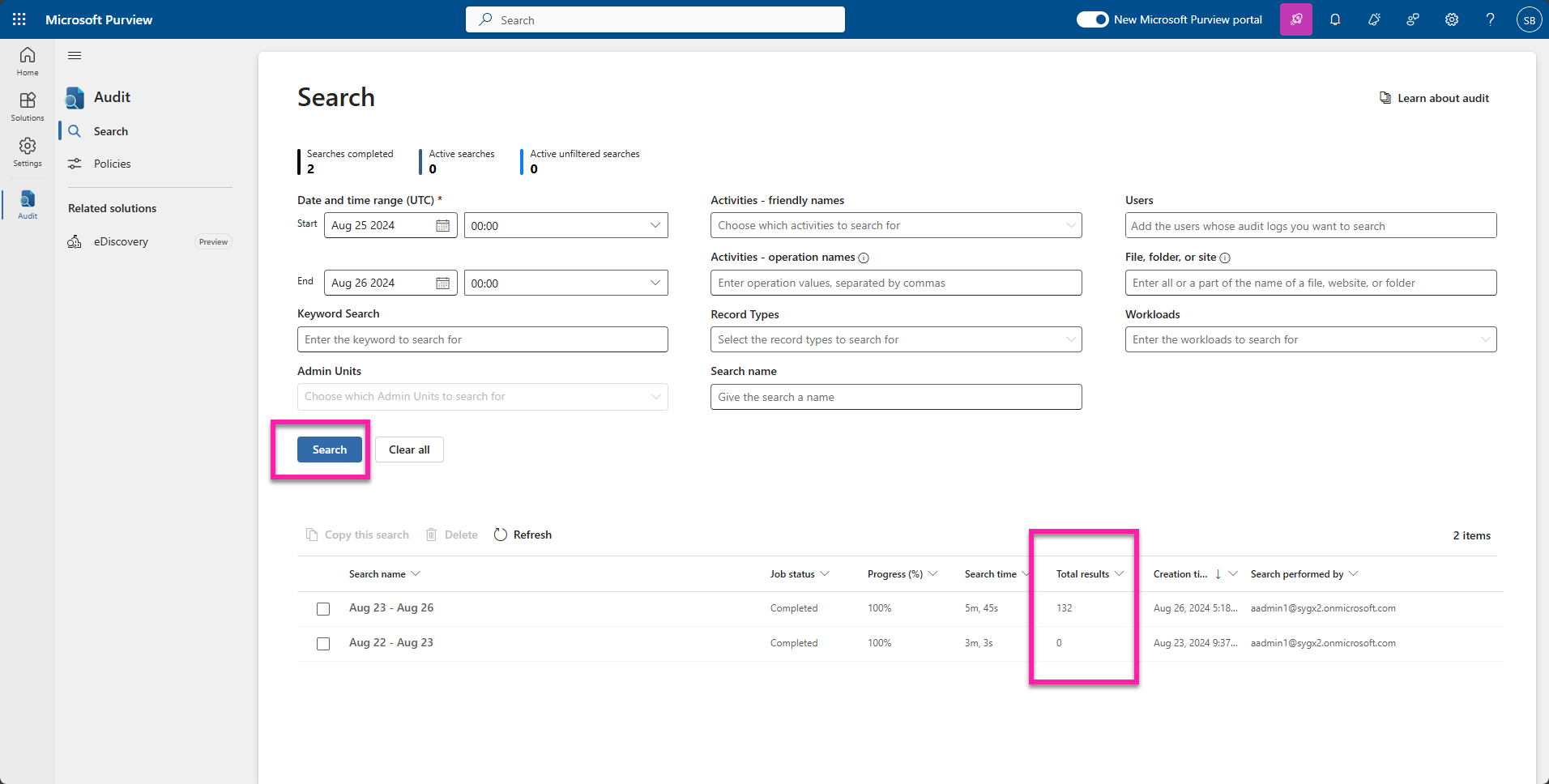
The first step is to clearly understand and define what you are looking for. You can start by defining the date range for your investigation and focus on key users or IP addresses. Narrow the results further to a specific service, like Exchange in the Workloads field. Go to the “Activities” dropdown to choose relevant actions and then combine these elements to formulate precise queries that will give you meaningful results.
| Query Filters and Fields | Description |
|---|---|
| Date and time range (UTC) | Date and time range (within scope of license) |
| Keyword Search | Terms searched within indexed content |
| Admin Units | Within specified Admin Units (if available) |
| Activities - friendly names | Drop-down menu of various events |
| Activities - operations names | Exact match of operation names (use commas for multiple) |
| Record types | Drop-down menu of specific record types |
| Search name | Not a filter – the name of this query |
| Users | Search users from the directory |
| File, folder, or site | URL or name corresponding to files, folders, or sites |
| Workloads | Drop-down menu of various services (ex. Exchange) |
When you get your results, you may need to use filters or advanced search option to process the data. If you’re investigating suspicious activities, go to the “Users” field to focus on specific accounts. These filters will allow you to drill down into the data and discover patterns or anomalies.
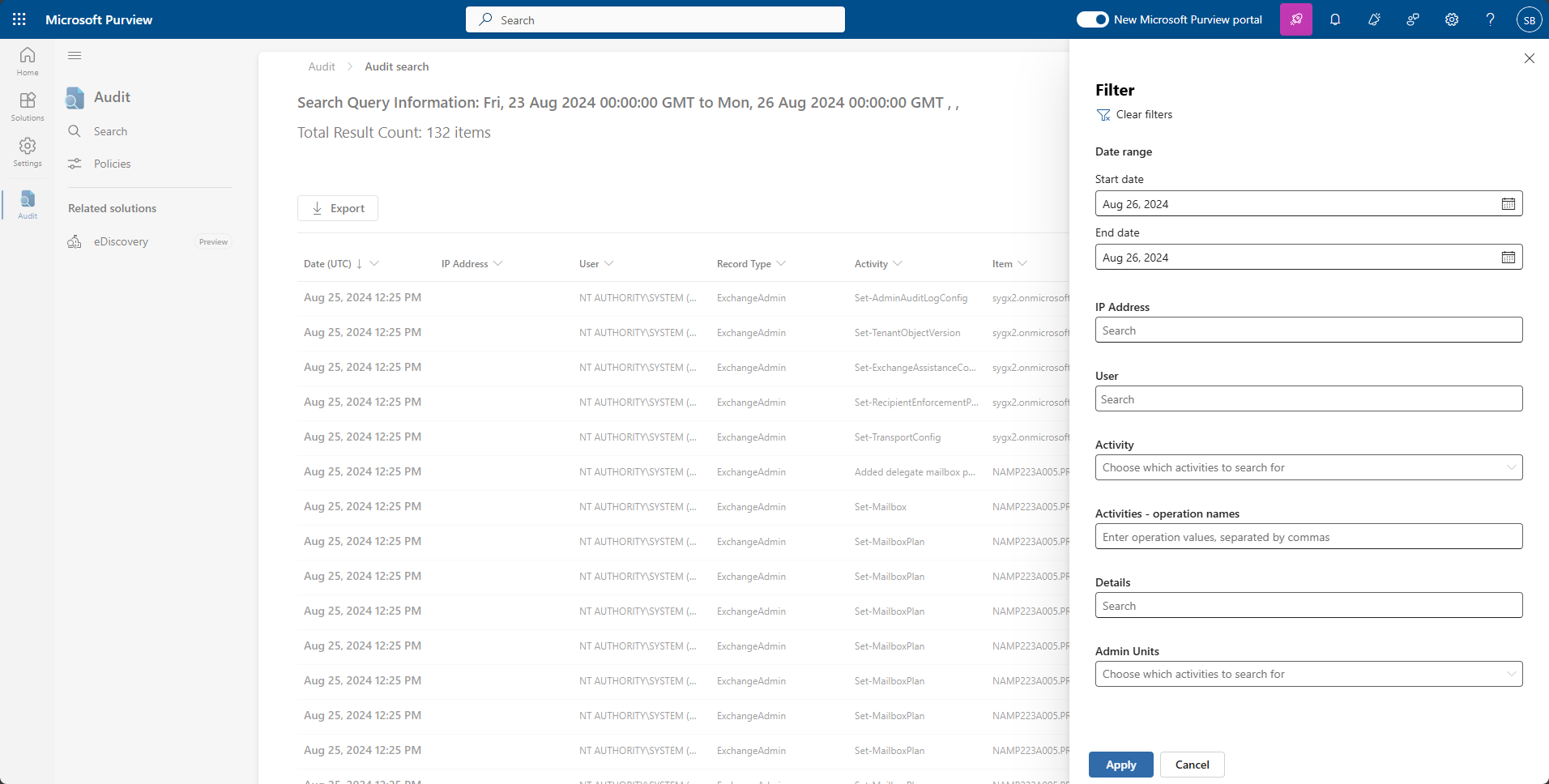
Interpreting search results
Once you ‘ve obtained and filtered your results to your satisfaction, the next step is to interpret the data. Go to the “Activity” column to see the specific action, while the “Item” column will give you context about the affected resource. If you want to identify unusual access locations, look at the “IP” address” field. The “Details” column contains valuable information about the activity. Make sure to look for outliers or patterns in the data that could show when a policy was not followed or another type of security issue.
To download your results to a CSV file, simply use the “Export” button. You can then use Excel or Power BI for deeper analysis. Convert the file to Excel and you can choose to create a pivot table to summarize activities by user or by type of action. By exporting regularly, you can create ongoing records for long-term trend analysis or for compliance reporting.
Understanding Audit Log Retention
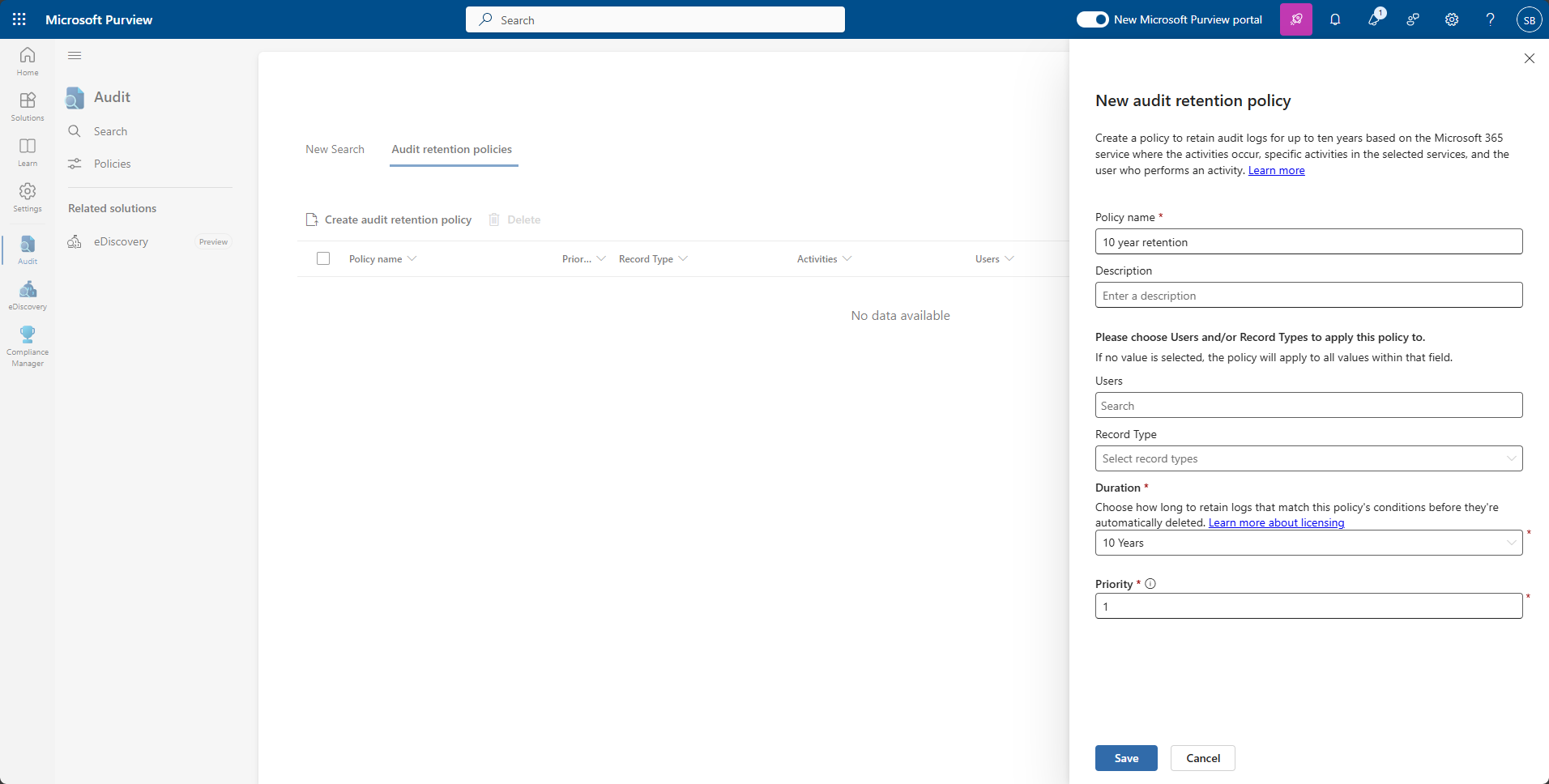
When using Office 365 audit logs, you will need to define a clear audit log retention policy to ensure compliance. With well- defined and thought-out retention policies, you’ll be able to access historical data for audit and investigation purposes.
| Limit | Audit log retention policies |
|---|---|
| 50 policies | Date and time range (within scope of license) |
| 180 days | Terms searched within indexed content |
| 365 days | Within specified Admin Units (if available) |
| 10 years | Drop-down menu of various events |
Default retention periods
When you are planning your log management strategy, you should be aware of your retention periods. The default retention periods will depend upon the type of Microsoft 365 subscription you have, but most plans keep audit logs for 90 days. If your users have Microsoft 365 E5 licenses, their logged activities will be retained for 180 days by default. The retention period can be extended up to a year. If you export your critical logs regularly, you can maintain records beyond the default retention period. Make sure to check the current retention settings in your tenant to make sure they are set to meet your compliance requirements.
The type of subscription will affect your log retention period, however there are other factors that will come into play, including your storage capacity and compliance needs. For example, high volume activities can generate a lot of log data and impact retention, so you may want to focus on critical activities, such as admin actions and events that are related to security. Aim for a balance between comprehensive coverage with storage limitations.
To customize log retention to fit your specific needs, go to the Security & Compliance Center to set up tailored retention policies based on specific groups, users or type of activity. For sensitive areas, like finance or executive accounts, you may want to consider longer retention periods.
License considerations for extended retention
You may want to upgrade from a basic plan with limited retention, to a higher-tier license to take advantage of the longer retention period and other advanced features. Ideally, you should perform a cost-benefit analysis of longer retention period against your compliance and security needs. If your organization has strict regulatory requirements, it may be worthwhile to invest in higher-tier licenses or an audit add on license. Another option is to implement a hybrid approach where you use advanced retention for critical areas and standard retention for operations that are not sensitive.
Key Use Cases
Office 365 audit logs are powerful tools that are ideal for Microsoft 365 IT admins who need to improve security, ensure compliance, optimize how their resources are allocated and want insight into the behaviour of their users.
- Compliance and regulatory requirements for regulations like GDPR and HIPAA often require very detailed tracking of user and admin actions to show that policies are being followed.
- Security incident investigations including repeated failed logins, changes in permissions or security settings, or unusual file access patterns.
- User behaviour analysis such as how employees use Microsoft 365 services, inefficient workflows, patterns in file sharing or how collaboration tools are used.
- Resource usage and adoption metrics like which Microsoft 365 features are the most popular among your users, the success of migration projects or rollouts of new products. All these insights will help guide Microsoft 365 IT planning, resource investment, license allocation and more.
Recommended Events to Monitor
Office 365 audit logs can track many activities, but there are certain events that you can prioritize so that you can ensure compliance, maintain strong security, identify threats quickly and take proactive action.
Critical administrative actions: The most common type of activities to monitor are critical admin actions. When monitoring these activities, make sure to watch for changes to user roles and permissions, especially those that grant elevated access. Look out for changes or creation of inbox rules, such as those that forward emails externally. Finally, keep an eye on changes to security settings, like updates to multi-factor authentication policies. By monitoring these activities, you’ll be alerted to changes that could compromise your environment. Managing your license assignments is another area where audit logs can be very useful.
Suspicious user activities: Some user activity can be signs of cracks in your security or violations of your policies. Your audit logs should be focusing on unusual patterns in file access, such as mass downloads or access from unfamiliar locations. Have your system alert you to multiple failed login attempts as this can be a sign of a security threat. Make sure you’re keeping track of changes to user account information, especially email addresses or password resets. These will help you pinpoint accounts that may be compromised.
Data access and sharing events: Office 365 audit logs are a great way to determine whether sensitive data is being shared outside of your organization. They should be tracking any changes in file and folder permissions, particularly changes that grant access to external users. For example, you can create a OneDrive sharing report for all users to see what is being shared. Additionally, you should look for unusual access to confidential information.
Authentication and authorization events: Authentication and authorization activities that should be monitored include login attempts from new devices or locations, as well as password changes and resets that may be potential account takeovers. Events related to MFA, such as enrollment changes or bypasses can be security risks and should be monitored.
Limitations of Native Office 365 Audit Logging
There are limitations to using native Office 365 audit logs. Recognizing these limitations and how they affect your strategy can help you find alternative methods or tools.
Search and reporting constraints: Microsoft 365’s native interface can only provide a maximum of 5,000 search entries which may not be enough for a large organization. However, the new Purview interface allows greater results. Exporting results is limited to 50,000 rows or 500,000 rows if you have a premium license. It takes a few minutes to download 22,282 rows.
With this mind, you may be required to section your searches into smaller time frames. You can also use PowerShell scripts to automate your data retrieval. You can then export and archive your logs regularly to keep a complete record. Alternatively, you can look for 3rd-party software tools that can provide a high number of search results.
Data visualization challenges: The native interface does not provide great graphical representation of your audit data making it more difficult to spot patterns. You will need to export the audit data to tools like Excel or Power BI so you can create intuitive and customized visualizations. Even then, parsing details is a major challenge if you want a proper analysis.
Real-time monitoring limitations: Native Office 365 office logging doesn’t alert you instantly if suspicious activities are detected. Unfortunately, this lack of real-time monitoring can delay your response time to critical issues. You can mitigate this by setting up scheduled searches and customized alert policies in the Security & Compliance Center.
Best Practices for Audit Log Management
Get the most value from your audit data by following best practices. These strategies will help you stay ahead of security risks.
Regular review of your audit log: Analyzing your logs should become a routine task as this will allow you to spot anomalies quickly. Establish a schedule for reviewing your audit logs and focus on areas that are high risk, such as access to sensitive data and admin actions. Use PowerShell or other 3rd-party tools to automatically extract data. Create your own custom reports that highlight trends and abnormalities. For more comprehensive reviews, assign different team members specific areas to review.
Establishing alerting mechanisms: Configure your process to include alerting policies so you will know when high-priority activities occur, including mass file downloads and repeated failed logins. You can do this in the Security & Compliance Center. Alerting mechanisms should be based on your organization’s risk profile and can include email notifications for your security team. Test and refine your alert settings so you can minimize false positives and focus on genuine security issues. Don’t hesitate to investigate other 3rd party tools for more advanced alerts. Some also offer the ability to schedule reports that can alert you about activities like log ins.
Documenting and reporting on audit findings: Clearly communicate findings and recommended actions by creating templates for your audit reports. If the data is difficult to understand, use data visualizations tools when sharing with other stakeholders. To identify recurring issues more easily, maintain a log of all investigations and outcomes. This will also help with compliance.
Continuous improvement of audit strategies: Defining your Office 365 audit log strategy is not a “one and done” type of activity. You should strive for continuous improvement of your processes, so they recognize new threats and align with new compliance requirements. Stay up to date on new features within native tools and keep abreast of new 3rd-party tools on the market. Your Office 365 audit log strategy should be a dynamic system that is continually evolving to address ever-changing security threats.
Advanced Unified Audit Log Techniques
By leveraging advanced Office 365 audit log techniques, IT admins can gain deeper insights and even automate complex auditing tasks. Using PowerShell is one method to overcome the limitations of native tools.
You can also use PowerShell scripts for advanced log queries. For example, you can use the Search-UnifiedAuditLog cmdlet to perform complex searches and you can automate regular searches and data exports. You can then fine tune your searches with parameters like -StartDate, -EndDate, and -Operations. Finally, you can use 3rd-party tools to tackle the most difficult queries.
Enhancing Audit Capabilities with Third-Party Tools
There are a few specialized audit and security solutions available that offer impressive features. One such tool is sapio365 which offers a unique interface to your Microsoft 365 data, including the Admin Audit Log. With sapio365, you are able to get an extensive view of all your user data in one place, without any pagination issues. Once the data is at your fingertips, you can use sapio365’s many filters and parameters to organize the data however you want.
Features to look for in third-party audit tools
sapio365 is an amazing tool for creating customized reports quickly and easily. Each view and report can be saved for future use and its automation features means you can create a report, save it and have it run on whatever schedule you choose. There are no scripts to worry about because everything is done with a few clicks.
You can create unlimited custom roles on Microsoft 365 with sapio365’s role-based access control (RBAC). You can customize roles to have actions and target sets that are exactly as wide or as narrow as you need so you can delegate tasks securely. The jobs that may have required a PowerShell expert can be delegated to the helpdesk or non-IT staff without PowerShell expertise.
sapio365 gives you the chance to preview any changes before you commit to them. Unlike PowerShell, you can be sure of what is being modified without the risk of an unexpected error occurring and wreaking havoc with your tenant.
Most importantly, sapio365 is not cloud-based but uses cloud-based information. All the information that sapio365 processes remains on your machine. You never need to worry about third parties, hosting, proxies. No other organization will have access to your data.
Conclusion
Office 365 audit logs are a method of reviewing actions and looking for anomalies that can indicate risky behaviours. To ensure compliance, maintain strong security, identify threats quickly and take proactive action, audit log strategies need to be developed, and the logs reviewed regularly.
There are limitations to the native tools but by using PowerShell or other 3rd-party tools, you can leverage many additional features that will help make your ongoing audit log management a success.
blog_sapio365





Submit a comment