Removing Weak Microsoft Office 365 Multi Factor Authentication Methods
A large part of an IT admins’ responsibilities is to make sure that users can sign in securely using approved Microsoft Office 365 multi factor authentication methods. To minimize the threat of a cybersecurity attack, you need to pinpoint the users with weak MFA methods so you can reset them. The problem is that the Microsoft admin portal does not make it easy to find these users or to remove weak Microsoft Office 365 Multi Factor Authentication methods.
Most IT admins will turn to using PowerShell scripts to help them identify the users and then reset their authentication methods. However, the problem is that an elaborate script is required to retrieve the users, make the necessary changes to improve security, and then verify that the changes were made properly. You need to have good coding skills to create that type of a PowerShell script and have a lot of confidence that it will do the job correctly. Luckily, there is now an option for IT admins who lack PowerShell coding skills. That option is sapio365, a PowerShell alternative that is easily available and requires no coding knowledge.
Let’s look at the two alternatives in more detail:
Option 1: Using PowerShell to retrieve MFA methods set by Microsoft 365 users
If you were to create a PowerShell script to list a single user’s MFA authentication methods, you would use MSOnline PowerShell to expand on the results of the cmdlet to retrieve a user’s properties, or you can connect to Microsoft Graph PowerShell.
MSOnline PowerShell
Get-MsolUser -ObjectID 1234userid56789 | Select StrongAuthenticationRequirements,StrongAuthenticationMethods,StrongAuthenticationUserDetails,StrongAuthenticationPhoneAppDetailsFAData.StrongAuthenticationUserDetails
Microsoft Graph PowerShell:
Get-MGUserAuthenticationMethod -userid username@domain.com | fl
Neither of these PowerShell methods is an easy feat. Incorporating the code snippets above into a script requires coding skills, patience and quite a bit of time. Keep reading to learn about our PowerShell alternative – sapio365 is a tool that can get you this information with just a couple of mouse clicks.
Option 2: Retrieving users with weak Microsoft Office 365 Multi Factor Authentication methods in less time
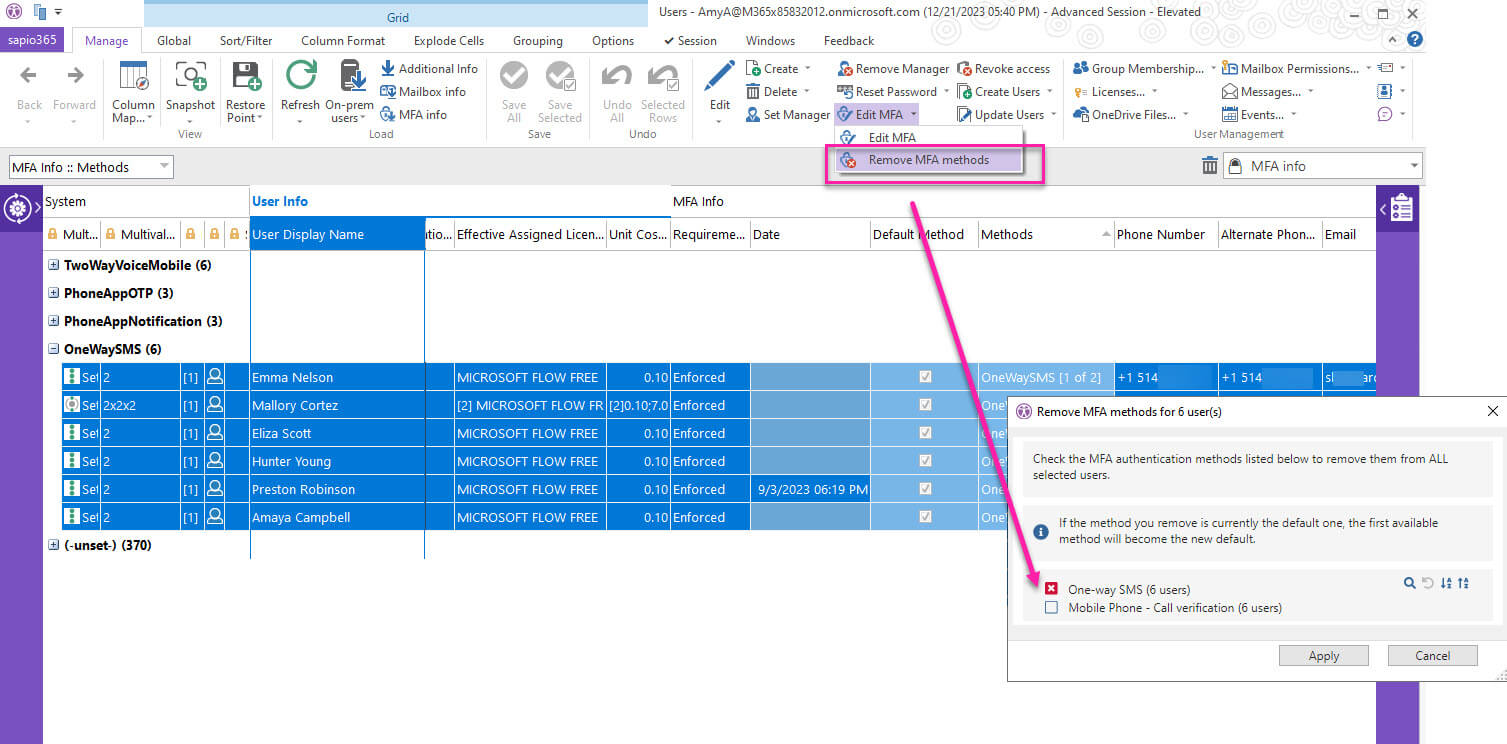
With sapio365, you can quickly get a global view of all the users and their chosen MFA methods, all in one place. With this information at hand, you can filter out users with approved methods to get a summary of all the users with weak methods (for example, SMS). Then you can select them all and force them to reregister the next time they sign into Microsoft Office 365.
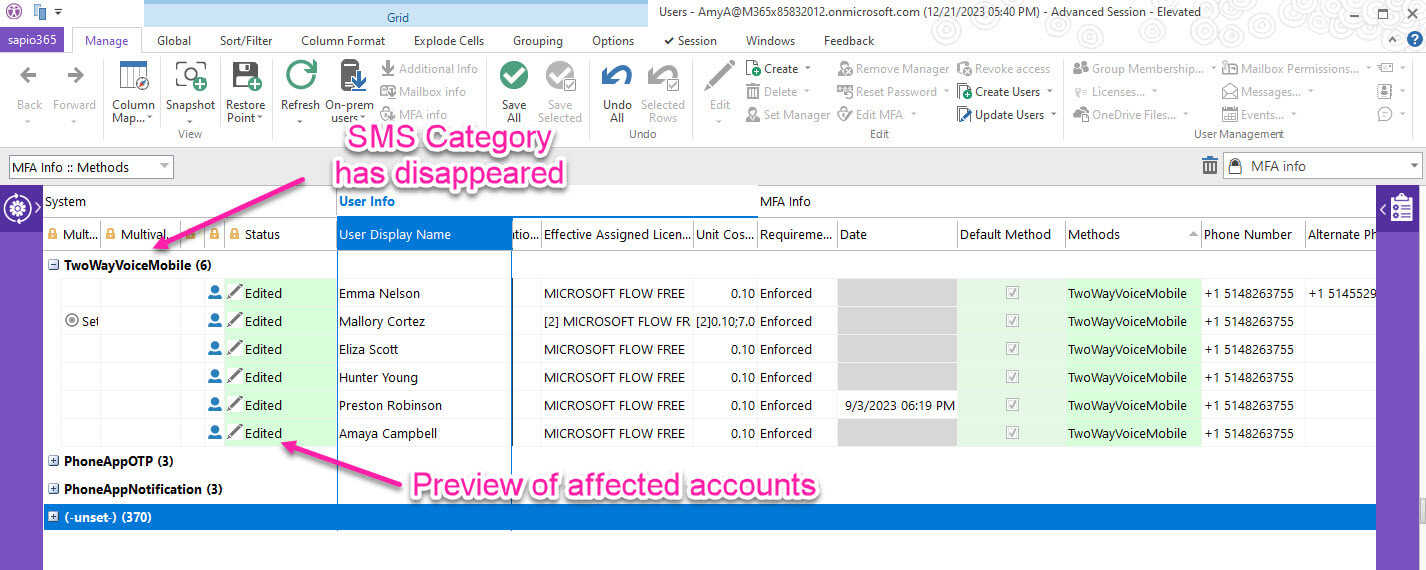
The sapio365 option is very quick and easy. If you have 100 users, the whole process will take you less than five minutes. What’s more, you won’t have to worry about making any manual errors because you can preview all your changes before saving them.
If you happen to be an IT admin who is not comfortable writing PowerShell scripts, removing weak Microsoft Office 365 multi factor authentication methods can be a daunting task that can cause you unnecessary stress. There will be a lot of trial and error, along with hopes and prayers for success. Even if you are a PowerShell expert, there is still a risk of errors being made. With sapio365, you gain the ability to preview your changes before you save them. This effectively eliminates the chance of mistakes being made. And the time you save can be spent on other value-added important tasks. Read how one happy customer easily found and eliminated MFA gaps in her tenant.
blog_sapio365

Submit a comment